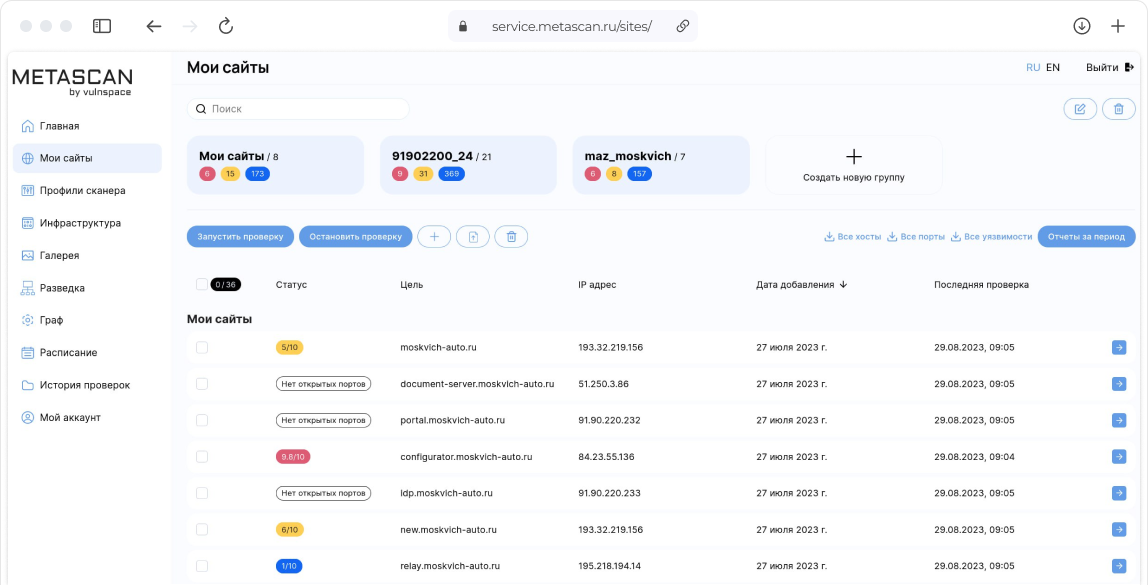
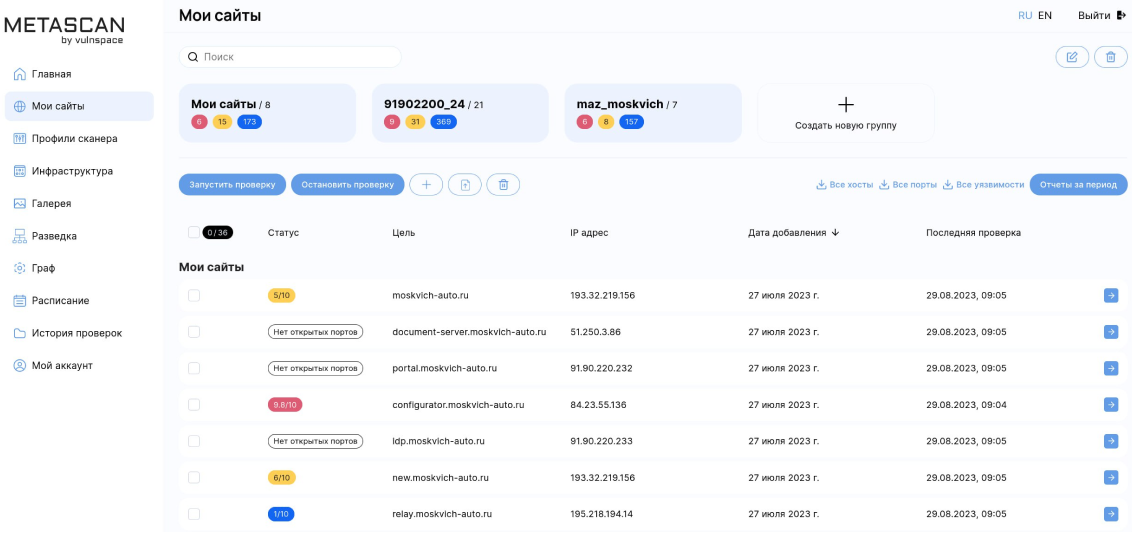
???
???
???
???
???
???
???
???
???
???
???
???
???
???
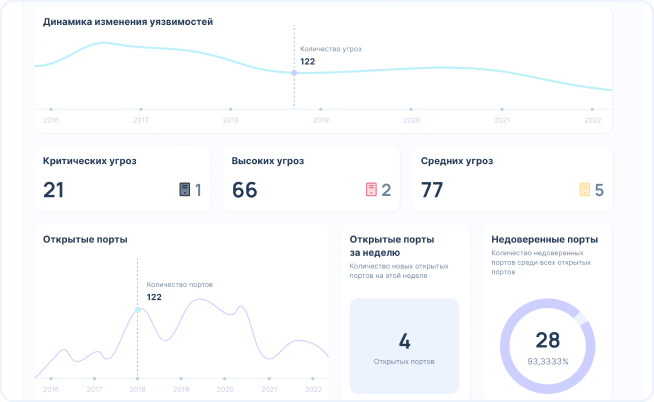
???
???
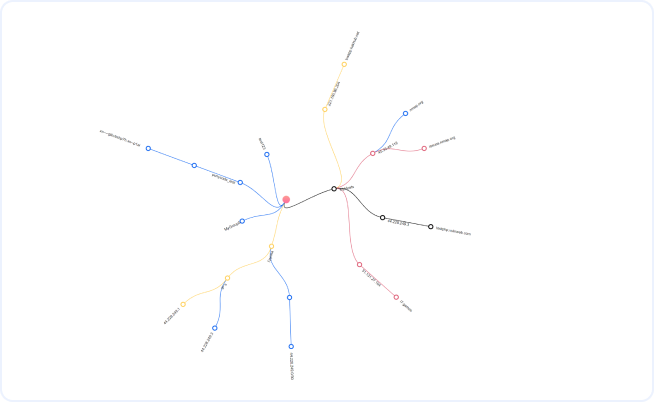
???
???
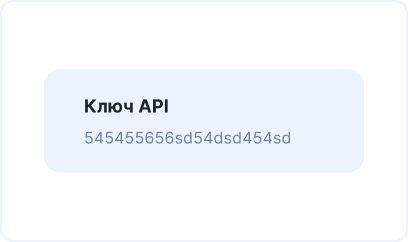
???
???
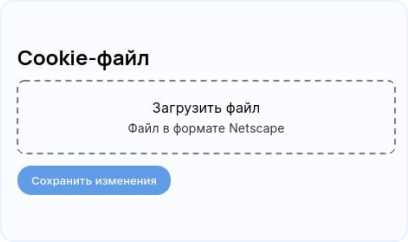
???
???
???
-
1???
-
2???
-
3???
-
4???
-
5???
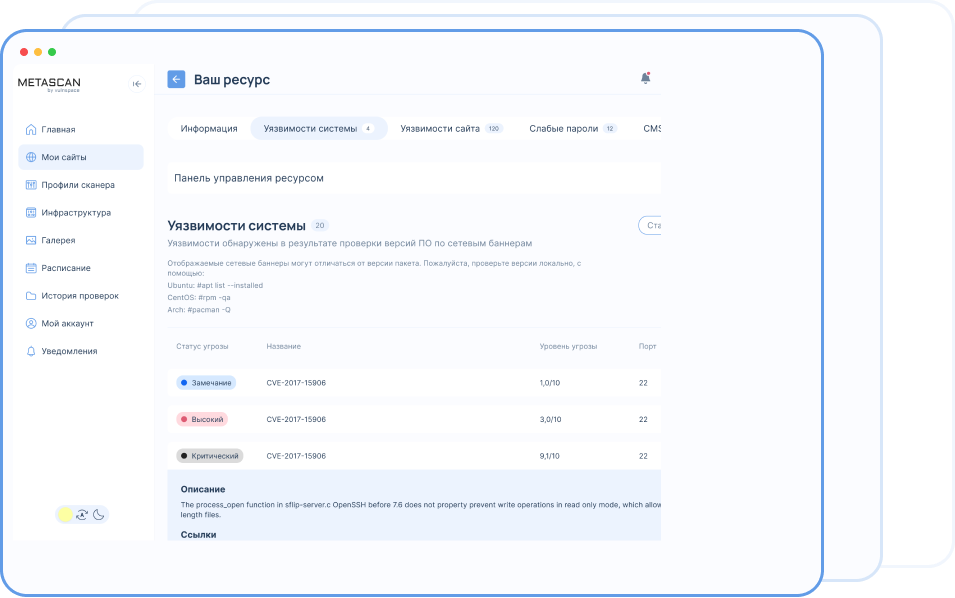
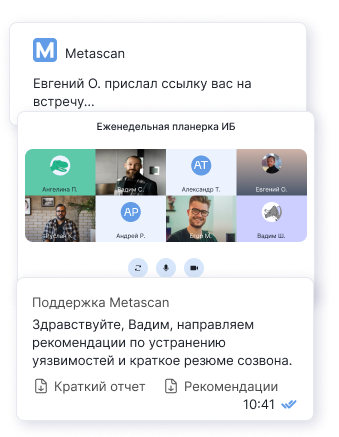
???
???
-
???
-
???
-
???
-
???
???
???
???
???
???
- OSI 3
- ???
- ???
- ???
- ???
- ???
- ???
- ???
- ???
- ???
- ???
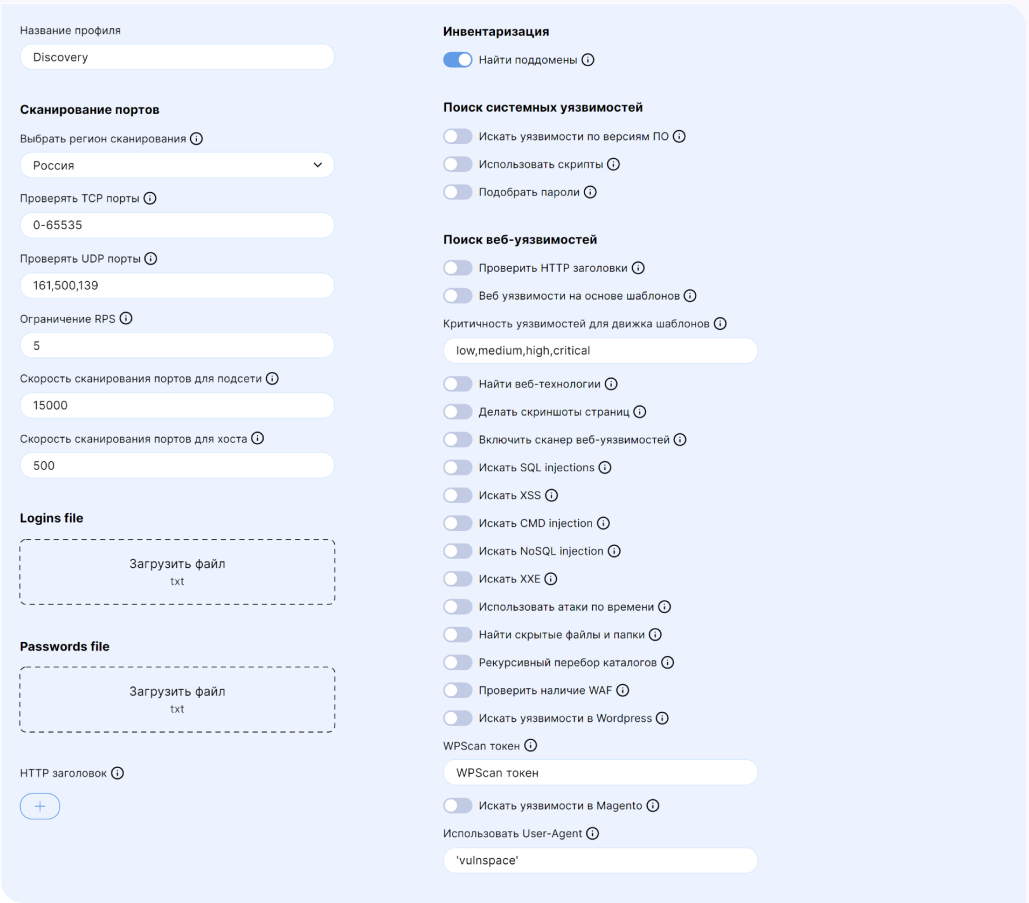
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
???
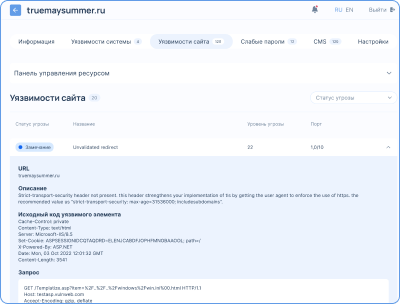
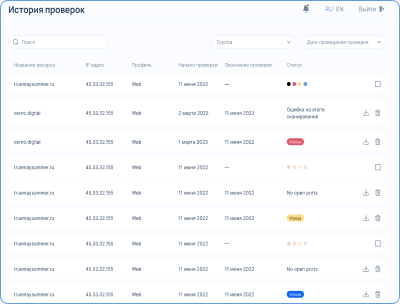
???
???
???
???
???
???
???